Trusted by





































Powered by PCYSYS
As part of the penetration test, all exploitation and dynamic hacking techniques are attemptep: sniffing MitM, lateral movement, remote execution, target DoD, password cracking, ethical malware injection, and privilege escalation.





































As your company’s attack surface continues to grow, you must focus remediation efforts on the vulnerabilities that matter most - the vulnerabilities that would be exploited by hackers in an attack.
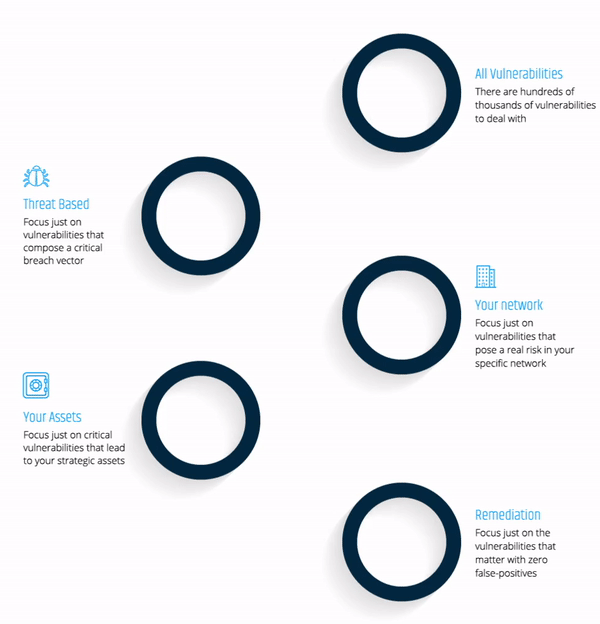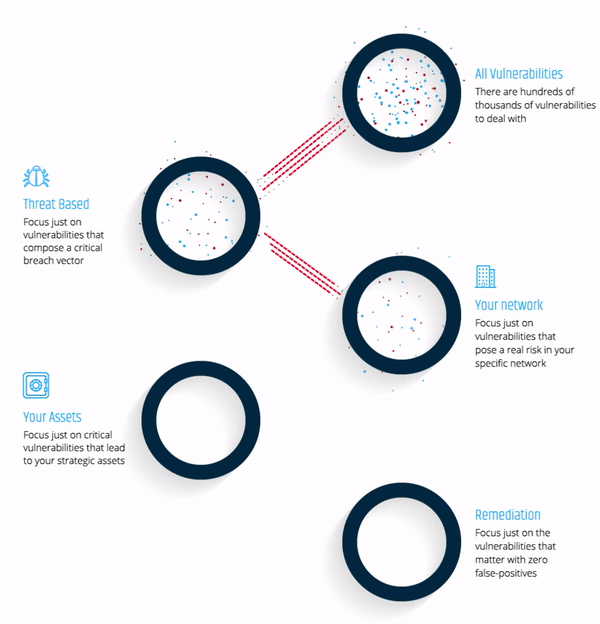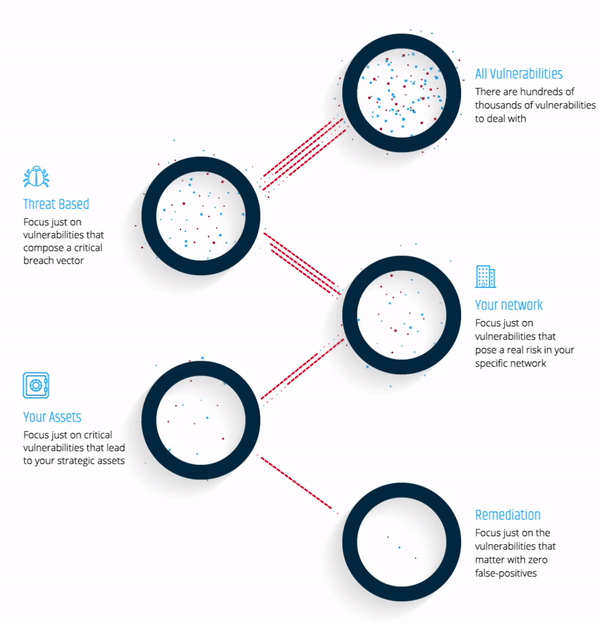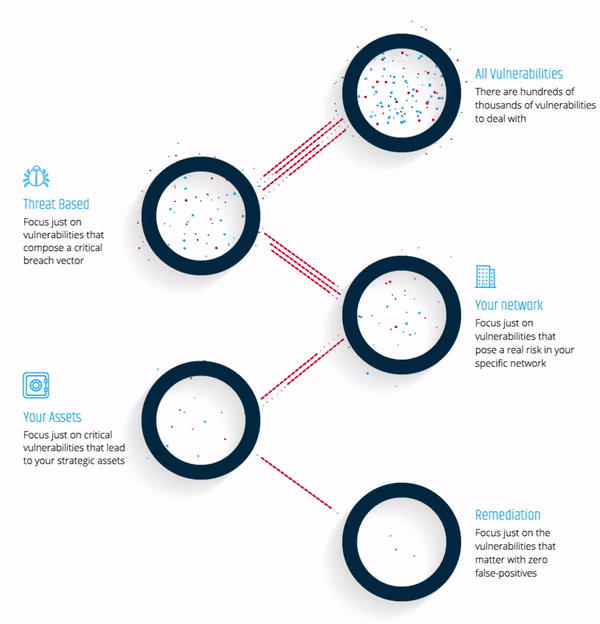

Read this datasheet and gain a deeper understanding of an attacker's mindset.